FBI Your Computer Has Been Locked is a screen locker which is created
by Internet criminals with the intention of tricking unsuspecting PC
users into paying a non existent fine for copyrighted material
supposedly detected on their computers. This scam exploits the name of
Federal Bureau of Investigation to make it seem more realistic. Notice
that FBI has never used and doesn't use such screen lockers to fight
Internet piracy, this screen locker was created by Cyber criminals who
are hoping that you will fall for this trickery and you will pay a non
existent fine to unlock your PC.
This scam is just one of many that attacks computers connected to the
Internet, previously seen screen locker which also exploited the name
of FBI and uses MoneyPak for payment was named The FBI Federal Bureau of Investigation.
Internet criminals also uses a name of McAfee and a badge "This site is
secure" to further trick PC users into believing that this screen
locker is legitimate. You shouldn't trust this screen, none of the
authorities are using such methods to collect fines for copyrighted
material. Note that MoneyPak is used to pay the supposed fine to make
the tracing of Internet criminals almost impossible. There are several
variants of this scam, both uses MoneyPak and has similar deceptive
messages.



FBI "Your computer has been locked" is a scam, don't pay the
imaginary fine, you will send your money to Cyber criminals who are
responsible for releasing this misleading screen locker. If your
computer screen has been locked by this message use the provided removal
instructions to eliminate it.
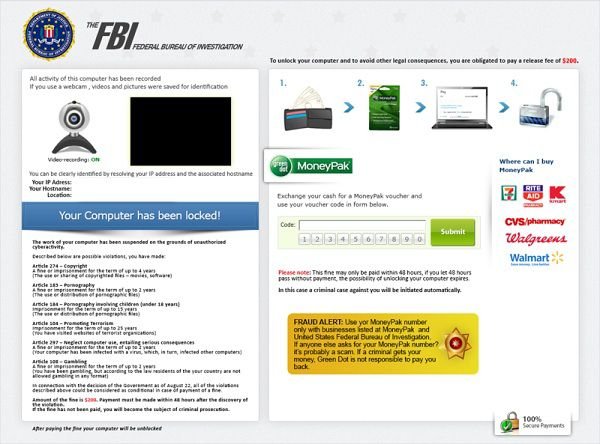
Fake message shown in FBI "Your computer has been locked" scam:
All activity of this computer has been recorded. If you use a
web cam videos and pictures were saved for identification. You can be
clearly identified by resolving your IP address and the associated host
name. Illegally downloaded material (MP3's, Movies or Software) has been
located on your computer. By downloading those were reproduced, thereby
involving a criminal offense under Section 100 of the Copyright Act.
The downloading of copyrighted material via the Internet or music
sharing networks is illegal and is in accordance with Section 100 of the
Copyright Act subject to a fine or imprisonment for a penalty of up to 3
years.
Furthermore, possession of illegally downloaded material
is punishable under Section 184 paragraph 3 of the Criminal Code and may
also leed to the confiscation of the computer, with which the files
were downloaded.
To unblock your computer and to avoid other
legal consequences you are obligated to pay a release fee of $200
Payable through GreenDot MoneyPak. After successful payment your
computer will automatically unlock. Failure to adhere to this request
could involve criminal charges and possible imprisonment.
FBI "Your computer has been locked" screen locker removal:
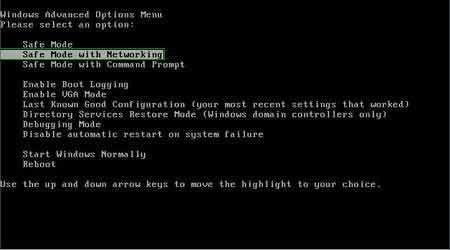
Step 1
During your
computer starting process
press F8 key on your
keyboard multiple times until
Windows Advanced Options
menu shows up, then select Safe
mode with networking from
the list and press ENTER.
Step 2
Log in to the account that is infected
with FBI "Your computer has been locked" scam. Start your Internet
browser and download a legitimate anti-spyware program. Update the
anti-spyware software and start a full system scan. Remove all the
entries that it detects.
Can't boot in Safe Mode with Networking? (FBI "Your computer has been locked" virus blocks Safe Mode with Networking)
If you have more than one user account
in your operating system - please log-in to the clean account and
download the recommended anti-spyware software, install it and run a
full system scan, remove all the security infections it will detect,
however if you have only one user account please follow this guide
(this guide will show you how to create a new user account using safe
mode with command prompt - using this newly created user account you
will be able to remove FBI "Your computer has been locked" ransomware).
If FBI "Your computer has been locked"
also blocks your operating system's Safe Mode with Networking follow
these removal instructions:
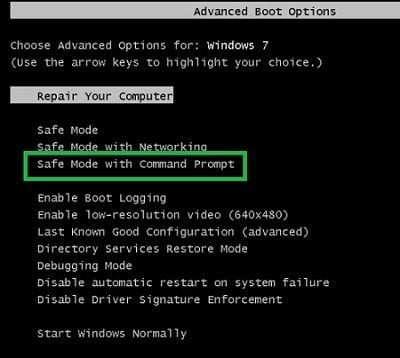
1. Start your computer in Safe Mode with Command Prompt
- During your computer
starting process press F8
key on your keyboard
multiple times until
Windows Advanced
Options menu shows up, then
select Safe mode with command
prompt from the list and press
ENTER.
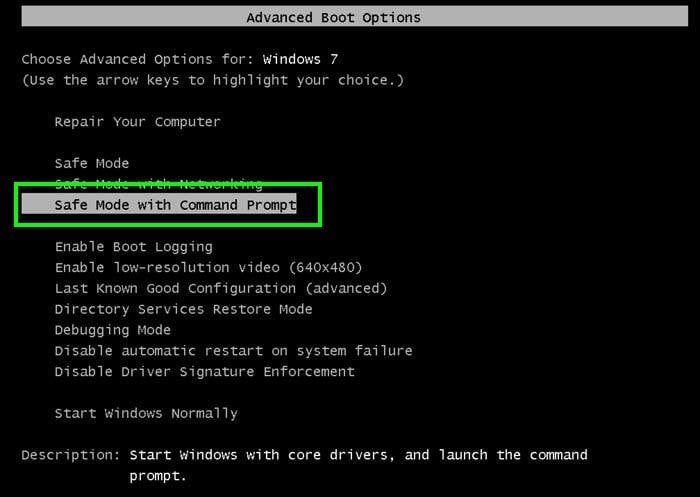
2. When command prompt mode loads enter the following line:
net user removevirus /add and press ENTER.
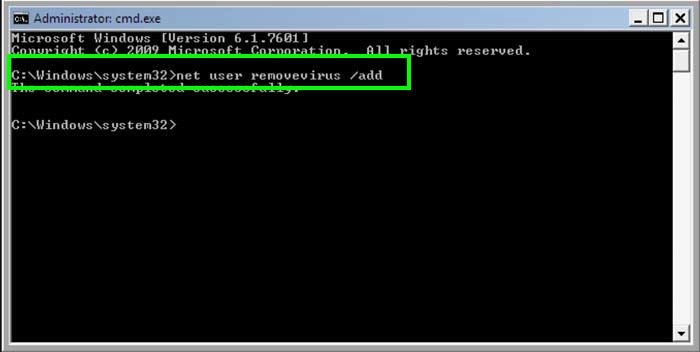
3. Next enter this line: net localgroup administrators removevirus /add and press ENTER.
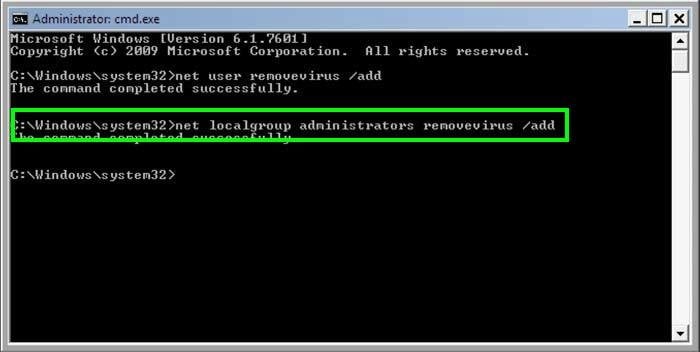
4. Finnaly enter this line:
shutdown -r and press ENTER.
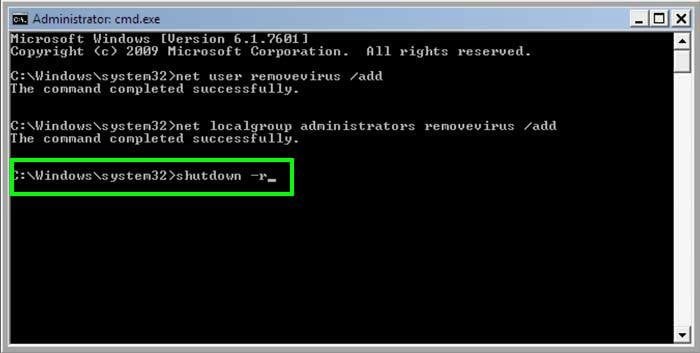
5. Wait for your computer to restart, then boot your PC in Normal
Mode and login to the newly created user account ("removevirus"). This
account won't be affected by the ransomware infection and you will be
able to download and install recommended anti-spyware software to
eliminate this virus from your computer.
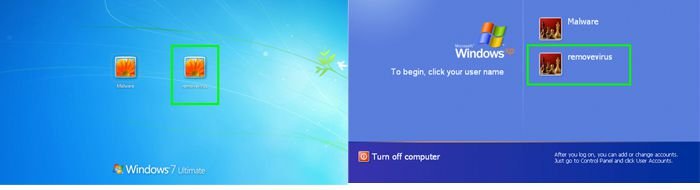
6. Download and install recommended anti-spyware software to eliminate this ransomware infection from your computer:
Remover for FBI "Your computer has been locked" virus
If the newly created user account is also affected by the ransomware infection try doing a System Restore:
1. Start your computer in Safe Mode
with Command Prompt - During your computer
starting process
press F8 key on your
keyboard multiple times
until Windows
Advanced Options menu shows
up, then select Safe
mode with command prompt from
the list and press ENTER.

2. When command prompt mode loads enter the following line:
cd restore and press ENTER.
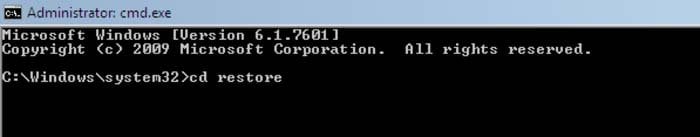
3. Next type this line:
rstrui.exe and press ENTER.
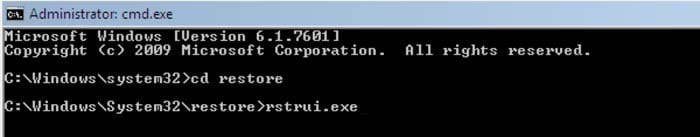
4. In the opened window click "Next".
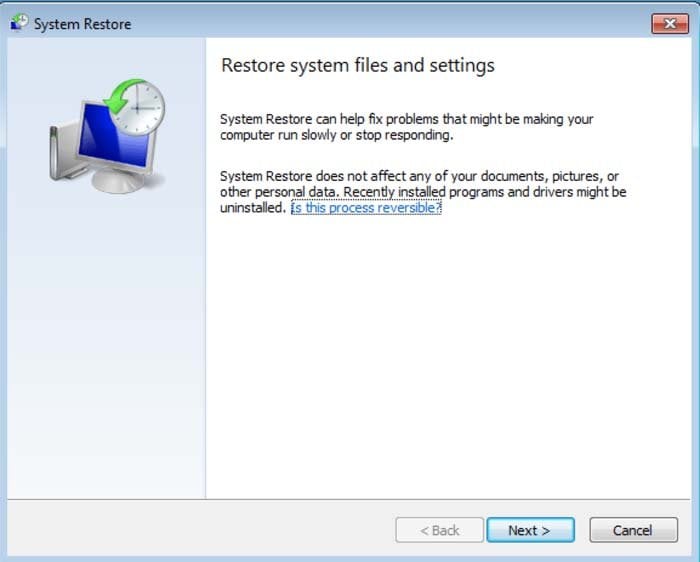
5. Select one of the available restore point and click "Next" (this
will restore your computer's system to an earlier time and date, before
the ransomware infiltrated your PC).
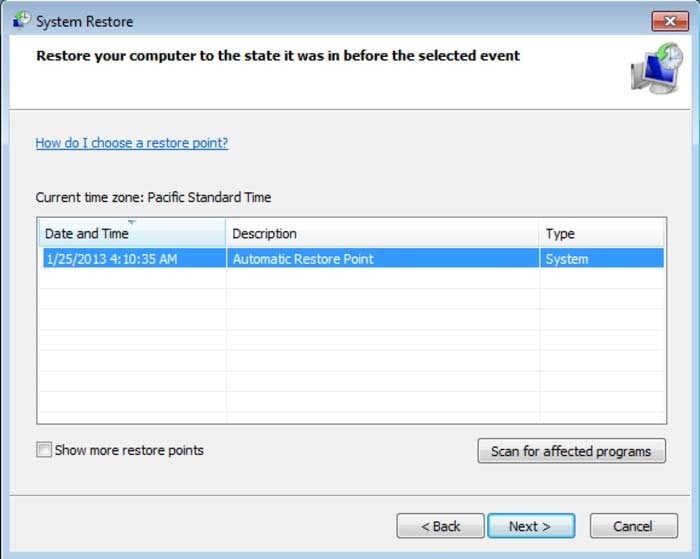
6. In the opened window click "Yes".
7. After restoring your computer to a previous date download and scan your PC with a
recommended anti-spyware software to eliminate any left remnants of "FBI - Your computer has been locked" ransomware.
Alternative FBI "Your computer has been locked" scam removal guide:
If this ransomware blocks your screen
when you start your computer in safe mode with networking, try starting
your PC in safe mode with command prompt.
1. During your
computer starting process
press F8 key on your
keyboard multiple times until
Windows Advanced Options
menu shows up, then select Safe
mode with command prompt from the
list and press ENTER.
2. In the opened command prompt type explorer and press Enter. This command will open explorer window, don't close it and continue to the next step.
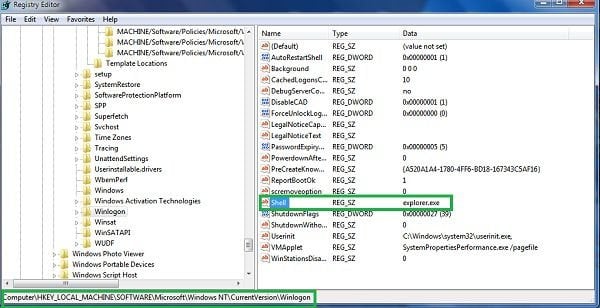
3. In the command prompt type regedit and press Enter. This will open the registry editor window.
4. In the registry editor window you should navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\
5. In the right side of the window
locate "Shell" and right click on it. Click on Modify. The default
value data is Explorer.exe if you see something else written in this
window remove it and type in Explorer.exe (you can write down whatever
else was written in the value data section - this is a path of the rogue execution file) - use this information to navigate to the rogue executable and remove it.
6. Restart your computer, download and
install a legitmate anti-spyware software and perform a full system
scan to eliminate any left remnants of FBI "Your computer has been
locked" scam.
If you can't start your computer in safe mode with networking (or with command prompt) you should
boot your computer using a rescue disk.
Some variants of ransomware disables safe mode making it's removal
more complicated. For this step you will need access to another
computer. After removing FBI "Your computer has been locked" scam from
your PC restart your computer and scan it with a legitimate antispyware
software to remove any possibly left remnants of this security
infection.
Other tools known to remove FBI "Your computer has been locked" scam:
Some
malicious software modifies browser settings and
disables
downloads of spyware and virus
removing software. If you
have problems downloading
anti-spyware software with
Internet Explorer, try
downloading with Chrome,
FireFox, Opera, etc.
If you can't access Internet:
Load your
computer in safe
mode. Click Start, click Shut
down, click Restart,
click OK. During your
computer starting process
press F8 key on your
keyboard multiple times until you
see Windows Advanced
Option menu, then select
Safe mode with networking
from the list.
Start
Task manager. Press ctrl+alt+del (or ctrl+shift+esc) and
end
task the processes of rogue program.
( if after this
procedure you can't access
any programs press
ctrl+alt+del, click File, select
New Task, and type
explorer.exe then press OK.
Open
Internet
explorer, click Tools and
select Internet Options. Select
Connections, then click
LAN settings, if a Use a
proxy server for your LAN
is checked, un-check it
and press OK.
After
this procedure you should
be able to access Internet.
Now you can download
anti-spyware software from
our "Top spyware
removers" section and run a
full scan. Download, install
and don't forget to
update your selected
anti-spyware program.